Published on: January 7, 2026
12 min read
OWASP Top 10 2025: What's changed and why it matters
Explore new supply chain and error handling risks, ranking shifts, and remediation strategies for all 10 categories.

The OWASP Foundation has released the eighth edition of its influential "Top 10 Security Risks" list for 2025, introducing significant changes that reflect the evolving landscape of application security. Based on analysis of more than 175,000 Common Vulnerabilities and Exposures (CVEs) records and feedback from security practitioners across the globe, this update addresses modern attack vectors. Here's everything you need to know about what's changed, why these changes matter, and how to protect your systems.
💡 Join GitLab Transcend on February 10 to learn how agentic AI transforms software delivery. Hear from customers and discover how to jumpstart your own modernization journey. Register now.
What's new in 2025?
The shift from 2021 (the last time the list came out) to 2025 represents more than minor adjustments, it's a fundamental shift in application security. Two entirely new categories entered the list and one category was consolidated into another, which highlights emerging risks that traditional testing often misses.
These additions and shifts can be seen in the chart below:
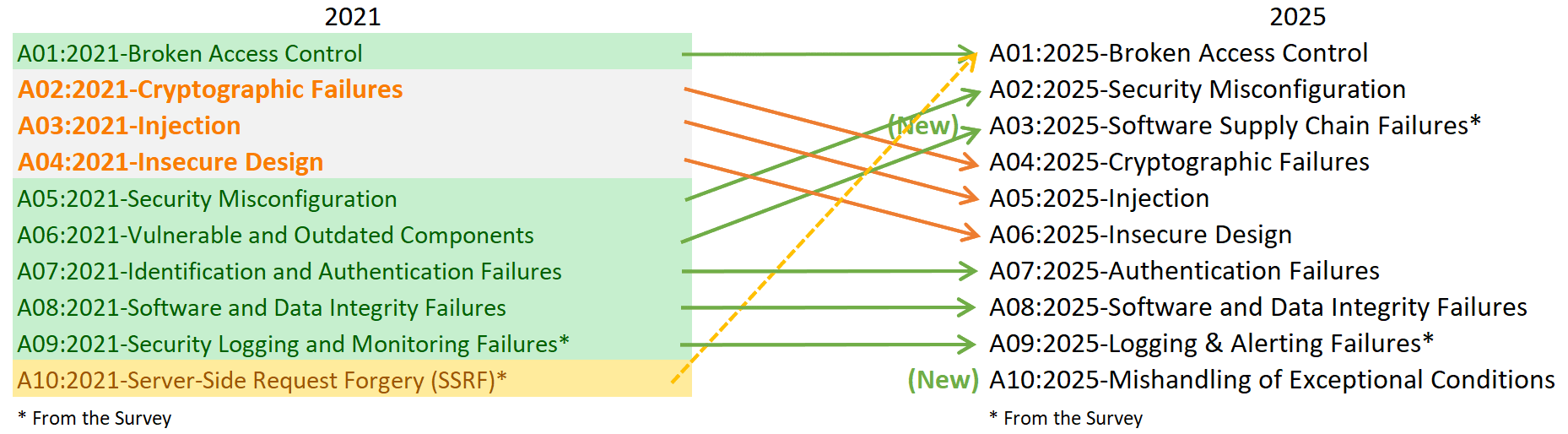
Two new categories
- A03: Software Supply Chain Failures: Expands the 2021 category "Vulnerable and Outdated Components" to encompass the entire software supply chain, including dependencies, build systems, and distribution infrastructure. Despite having the fewest occurrences in testing data, this category has the highest average exploit and impact scores from CVEs.
- A10: Mishandling of Exceptional Conditions: Focuses on improper error handling, logical errors, and failing open scenarios. This addresses how systems respond to abnormal conditions.
Major ranking changes
- Security Misconfiguration surged from #5 (2021) to #2 (2025), now affecting 3% of tested applications.
- Server-Side Request Forgery (SSRF) has been consolidated into A01: Broken Access Control.
- Cryptographic Failures dropped from #2 to #4.
- Injection fell from #3 to #5.
- Insecure Design moved from #4 to #6.
Why these changes were made
The OWASP methodology combines data-driven analysis with community insights. The 2025 edition analyzed 589 Common Weakness Enumerations (CWEs), which is a substantial increase from the approximately 400 CWEs in 2021. This expansion reflects the growing complexity of modern software systems and the need to capture emerging threats.
The community survey component addresses a fundamental limitation: testing data essentially looks into the past. By the time security researchers develop testing methodologies and integrate them into automated tools, years may have passed. The two community-voted categories ensure that emerging risks identified by frontline practitioners are included, even if they're not yet prevalent in automated testing data.
The rise of Security Misconfiguration highlights an industry trend toward configuration-based security, while Software Supply Chain Failures acknowledges the rise of sophisticated attacks targeting compromised packages.
Using GitLab Ultimate for vulnerability detection and management
GitLab Ultimate provides comprehensive security scanning to detect risks across the 2025 OWASP Top 10 categories. For instance, the end-to-end platform analyzes your project's source code, dependencies, and infrastructure definitions. It also uses Advanced Static Application Security Testing (SAST) to detect injection flaws, cryptographic failures, and insecure design patterns in source code. Infrastructure as Code (IaC) scanning finds security misconfigurations in your deployment definitions. Secret Detection prevents the leakage of credentials, and Dependency Scanning uncovers libraries with known vulnerabilities in your software supply chain, which directly addresses the new A03 category for Software Supply Chain Failures.
In addition:
- Dynamic Application Security Testing (DAST) probes your deployed application for broken access control, authentication failures, and injection vulnerabilities by simulating attack vectors.
- API Security Testing probes your API endpoints for input validation weaknesses and authentication bypasses.
- Web API Fuzz Testing uncovers how your application handles exceptional conditions by generating unexpected inputs, which directly addresses the new A10 category for mishandling of exceptional conditions.
Security scanning integrates seamlessly into your CI/CD pipeline, running when code is pushed from a feature branch so developers can remediate vulnerabilities before they reach production. Security findings are consolidated in the Vulnerability Report, where security teams can triage, analyze, and track remediation. GitLab also allows you to leverage AI agents such as Security Analyst Agent, available in GitLab Duo Agent Platform, to quickly determine what are the most critical vulnerabilities and how to take action on them.
You can enforce additional controls through merge request approval policies and pipeline execution policies to ensure security scanning runs consistently across your organization. Customer Success and Professional Services teams at GitLab ensure you derive value from an investment in GitLab in a timely manner.
Deliver secure software faster with security testing in the same platform developers already use. To learn more, visit our application security testing solutions site.
The OWASP Top 10 2025: Complete breakdown
A01: Broken Access Control
What it is
Failures in enforcing policies that prevent users from acting outside their intended permissions, leading to unauthorized access.
Impact on your system
- Unauthorized information disclosure
- Complete data destruction or data modification
- Privilege escalation (users gaining admin rights)
- Viewing or editing other users' accounts
- API access from unauthorized or untrusted sources
Notable CWEs
- CWE-22: Path Traversal
- CWE-200: Exposure of Sensitive Information to an Unauthorized Actor
- CWE-352: Cross-Site Request Forgery (CSRF)
A02: Security Misconfiguration
What it is
Systems, applications, or cloud services configured incorrectly from a security perspective.
Impact on your system
- Exposure of sensitive information through error messages
- Unauthorized access through default accounts
- Unnecessary services or features enabled
- Outdated security patches
- Server does not send security headers or directives
Notable CWEs
A03: Software Supply Chain Failures
What it is
Breakdowns or compromises in building, distributing, or updating software through vulnerabilities or malicious changes in dependencies, tools, or build processes.
Impact on your system:
- Compromised packages introducing backdoors
- Malicious code injected during build processes
- Vulnerable dependencies cascading through your application
- Use of components from untrusted sources in production
- Changes within your supply chain are not tracked
Notable CWEs
- CWE-1395: Dependency on Vulnerable Third-Party Component
- CWE-1104: Use of Unmaintained Third Party Components
A04: Cryptographic Failures
What it is
Failures related to lack of cryptography, insufficiently strong cryptography, leaking of cryptographic keys, and related errors.
Impact on your system:
- Sensitive data exposure (passwords, credit cards, health records)
- Man-in-the-middle attacks
- Data breach through weak encryption
- Key compromise leading to system-wide exposure
- Regulatory compliance failures (GDPR, PCI DSS)
Notable CWEs
- CWE-327: Use of a Broken or Risky Cryptographic Algorithm
- CWE-330: Use of Insufficiently Random Values
A05: Injection
What it is
System flaws allowing attackers to insert malicious code or commands (SQL, NoSQL, OS commands, LDAP, etc.) into programs.
Impact on your system
- Data loss or corruption through SQL injection
- Complete database compromise
- Server takeover through command injection
- Cross-site scripting (XSS) attacks
- Information disclosure
- Denial of service
Notable CWEs
A06: Insecure Design
What it is
Weaknesses in design representing different failures, expressed as missing or ineffective control design—architectural flaws rather than implementation bugs.
Impact on your system
- Weak password reset flows
- Missing authorization steps
- Flawed business logic allowing bypasses
- Inadequate threat modeling leading to blind spots
- Design patterns that fail under attack scenarios
Notable CWEs
- CWE-209: Generation of Error Messages Containing Sensitive Information
- CWE-522: Insufficiently Protected Credentials
- CWE-656: Reliance on Security Through Obscurity
A07: Authentication Failures
What it is
Vulnerabilities allowing attackers to trick systems into recognizing invalid or incorrect users as legitimate.
Impact on your system
- Account takeover and credential stuffing
- Session hijacking
- Brute force attacks succeeding
- Weak password recovery mechanisms exploited
- Multi-factor authentication bypass
Notable CWEs
- CWE-287: Improper Authentication
- CWE-306: Missing Authentication for Critical Function
- CWE-521: Weak Password Requirements
A08: Software or Data Integrity Failures
What it is
Code and infrastructure failing to protect against invalid or untrusted code/data being treated as trusted and valid.
Impact on your system
- Unsigned updates allowing malicious code injection
- Insecure deserialization leading to remote code execution
- CI/CD pipeline compromise
- Auto-update mechanisms exploited
- Tampered software artifacts
Notable CWEs
- CWE-345: Insufficient Verification of Data Authenticity
- CWE-346: Origin Validation Error
- CWE-347: Improper Verification of Cryptographic Signature
A09: Security Logging & Alerting Failures
What it is
Insufficient logging and monitoring with inadequate alerting, which makes rapid response difficult.
Impact on your system
- Attacks go undetected for extended periods
- Breach investigation becomes impossible
- Compliance violations from lack of audit trails
- Delayed incident response
- Inability to determine scope of compromise
Notable CWEs
- CWE-117: Improper Output Neutralization for Logs
- CWE-532: Insertion of Sensitive Information into Log File
- CWE-778: Insufficient Logging
A10: Mishandling of Exceptional Conditions
What it is
Programs failing to prevent, detect, and respond to unusual and unpredictable situations, which leads to crashes, unexpected behavior, or vulnerabilities.
Impact on your system
- Information disclosure through verbose error messages
- Denial of service from unhandled exceptions
- State corruption from improper error handling
- Race conditions exploited
- Systems failing open instead of closed
- Application crashes exposing sensitive data
Notable CWEs
- CWE-248: Uncaught Exception
- CWE-390: Detection of Error Condition Without Action
- CWE-391: Unchecked Error Condition
Prevention and remediation best practices
GitLab provides tools to enable you to not only quickly find and remediate vulnerabilities within the OWASP Top 10, but also to prevent them from making it into your production system. By following these best practices you can enhance and maintain your security posture:
Automated security scanning for all repositories
- Perform SAST Scanning to detect insecure design patterns like plaintext password storage, inadequate error handling, and missing encryption during code review, catching design flaws early in the development lifecycle.
- Perform Secret Detection to identify credentials in configuration files, environment variables, and code, preventing plaintext password storage and ensuring secrets are properly managed through GitLab's CI/CD variables with masking and encryption.
- Perform DAST Scanning to detect broken access control vulnerabilities
- Perform Dependency Scanning to scan project dependencies against vulnerability databases, identifying known CVEs in direct and transitive dependencies across multiple package managers (npm, pip, Maven, etc.).
- Perform Container Scanning to analyze Docker images for vulnerable base layers and packages, ensuring container supply chain security before deployment.
- Perform IaC Scanning to check your infrastructure definition files for known vulnerabilities.
- Leverage API Security Tools to secure and protect web APIs from unauthorized access, misuse, and attacks.
- Perform Web API Fuzz Testing to discover bugs and potential vulnerabilities that other QA processes might miss.
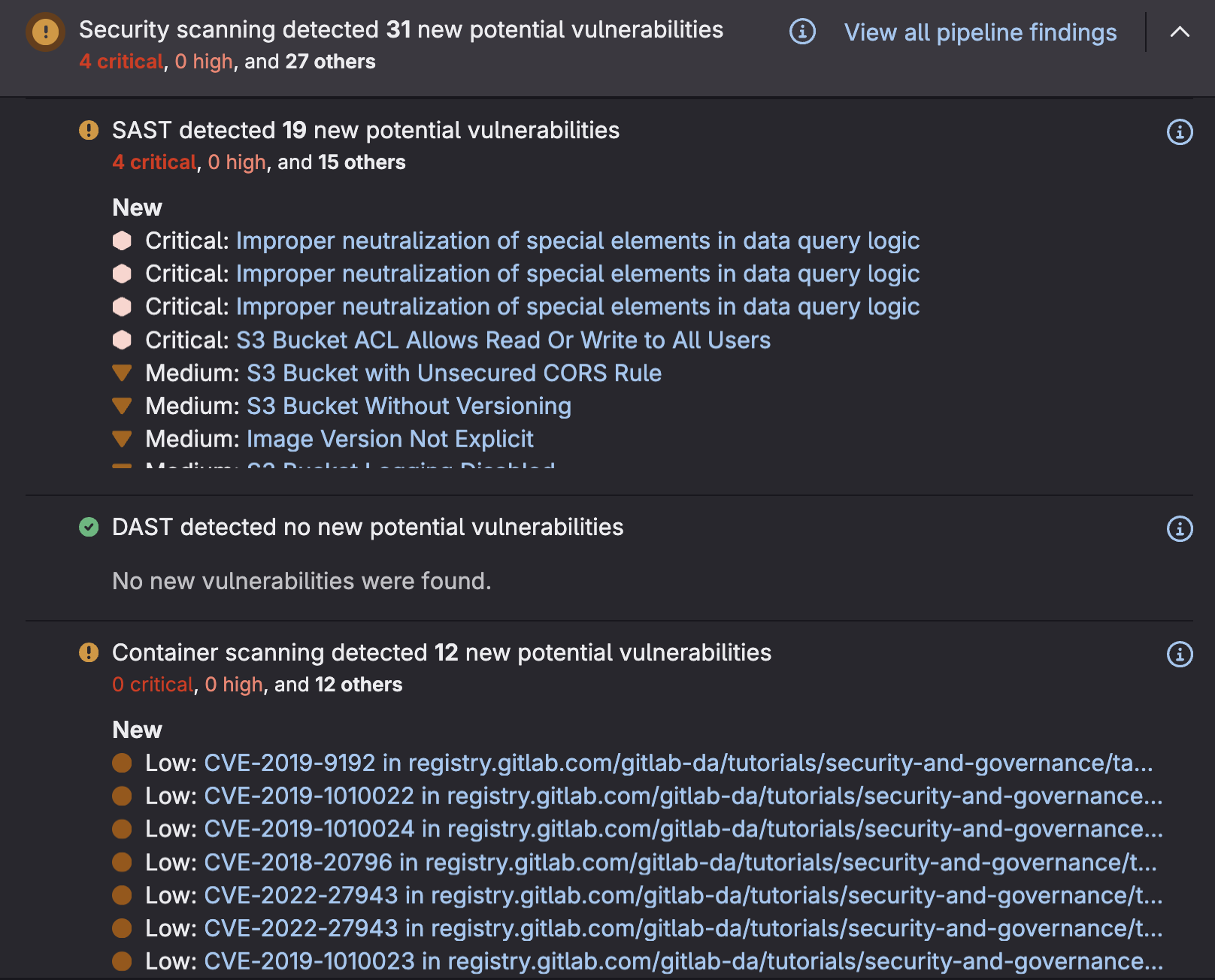
Understand your security posture
- Generate a software bill of materials (SBOM) for complete dependency visibility and compliance requirements.
- Leverage the Vulnerability Report to sort through and triage vulnerabilites via consolidated view of security vulnerabilities found in your codebase.
- Quickly take action on vulnerabilities using detailed remdiation guidance and risk assessment data.
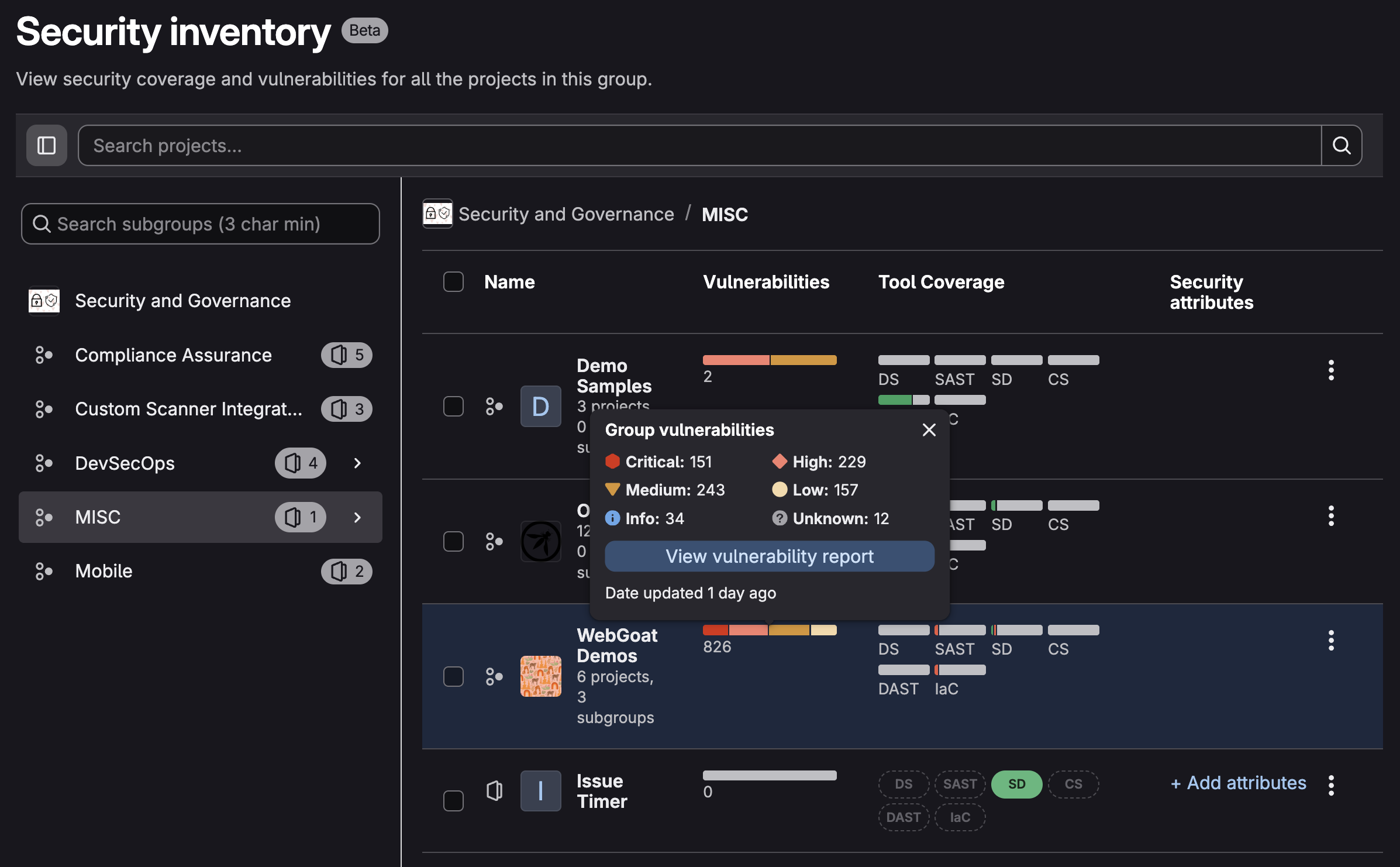
- Use Security Iventory to visualize which assets you need to secure and understand the actions you need to take to improve security.
- Leverage Compliance Center to manage compliance standards adherence reporting, violations reporting, and compliance frameworks.
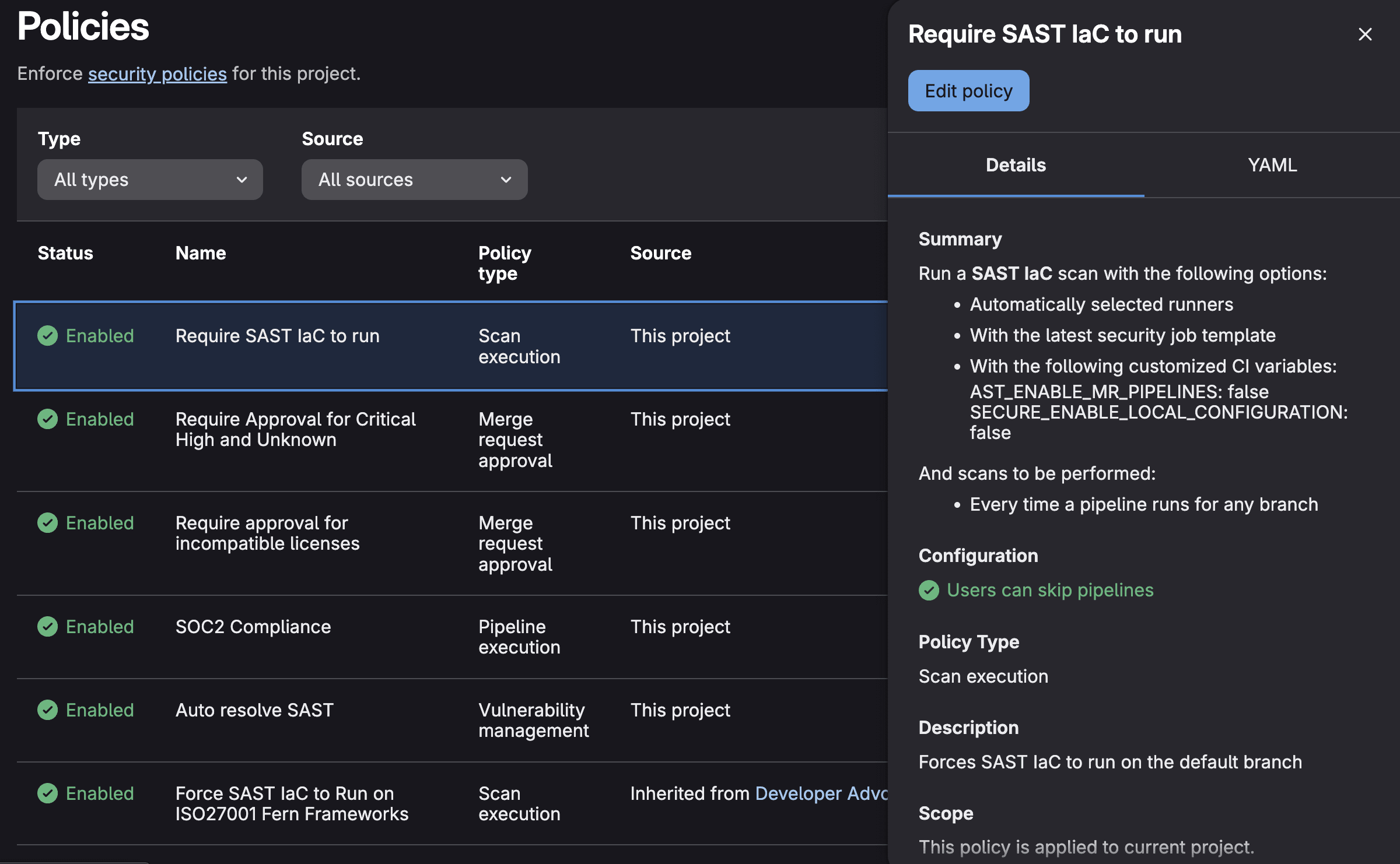
Set up prevention and maintain documentation
- Configure Security Policies to block merges or deployments when high-severity vulnerabilities are detected in dependencies, enforcing security standards automatically.
- Use Compliance Frameworks to enforce organizational security standards through automated policy checks that verify encryption requirements, credential management practices, and secure workflow implementations are followed.
- Use GitLab Wiki and repository documentation to maintain security design principles, approved patterns, and architectural decision records that guide developers toward secure-by-design implementations.
- Implement merge request approval rules requiring security architect review for features involving authentication, authorization, encryption, or sensitive data handling, ensuring design-level security validation.
- Create tests to verify input validation and allowlist approaches for file paths
- Use GitLab Issues and Epics to document security requirements and threat models during the design phase, creating a traceable record of security decisions and ensuring security considerations are addressed before implementation begins.
Leverage AI
- Use Code Suggestions for proactive guidance during development, suggesting secure design patterns like proper password hashing (bcrypt, Argon2), encrypted storage mechanisms, and appropriate error handling that doesn't leak sensitive information.
- Use Security Analyst Agent to review detected insecure design vulnerabilities in context, explaining the architectural implications, assessing risk based on your application's threat model, and providing remediation strategies that address root design flaws rather than just symptoms.
- Review your code using AI to help ensure consistent code review standards in your project.
Key takeaways for development teams
- Supply chain security is critical: With A03's addition and high-impact scores, securing your software supply chain is no longer optional. Implement SBOM tracking, dependency scanning, and integrity verification throughout your pipeline.
- Configuration matters more than ever: The rise to #2 shows that configuration-based security is now a primary attack vector. Automate configuration verification and implement IaC with security baked in.
- Traditional threats persist: While Injection and Cryptographic Failures dropped in ranking, they remain critical. Don't deprioritize them just because they've fallen on the list.
- Error handling is security: The new A10 category emphasizes that how your application handles failures is a security concern. Implement secure error handling from the start.
- Testing must evolve: The expanded CWE coverage (589 vs. 400 in 2021) means testing strategies must be comprehensive. Combine SAST, DAST, source code analysis, and manual penetration testing for effective coverage.
Explore our GitLab Security and Governance Solutions and security scanning documentation to start strengthening your security posture today.
We want to hear from you
Enjoyed reading this blog post or have questions or feedback? Share your thoughts by creating a new topic in the GitLab community forum.
Share your feedback