Improved GitLab Duo and SDLC trends dashboard
Improved GitLab Duo and SDLC trends dashboard
The GitLab Duo and SDLC trends dashboard delivers improved analytics capabilities to measure the impact of GitLab Duo on software delivery. The dashboard now provides 6-month trend analysis across GitLab Duo feature adoption, pipeline performance, and common development metrics such as deployment frequency and mean time to merge.
You can now track code generation volumes and IDE or language trends for GitLab Duo Code Suggestions, and observe as your teams adopt new GitLab Duo Agent Platform flows. Enhanced user-level metrics enable teams to gain deeper insight into the key Duo features providing continuous value.
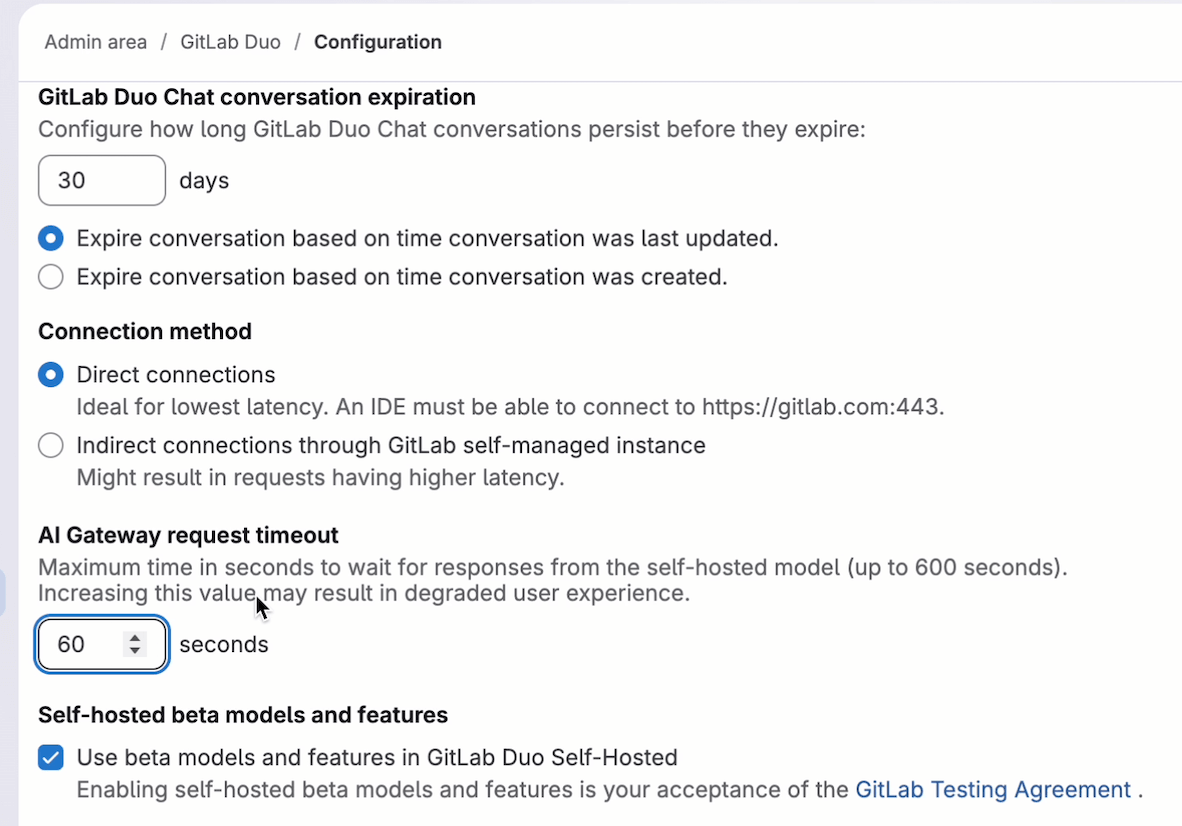
A new endpoint for instance-level AI usage is now available for instance administrators to extract all Duo data from either Postgres (3-month retention) or ClickHouse.
Powered by the ClickHouse integration, this dashboard delivers sub-second query performance across millions of data points. For self-managed instances, see improved recommendations and configuration guidance for ClickHouse integration.
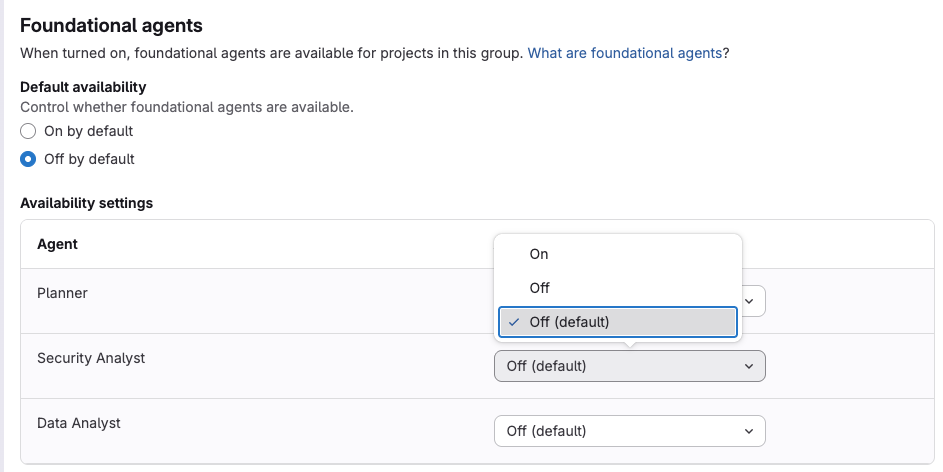
Additional Planner Agent features available in beta
Additional Planner Agent features available in beta
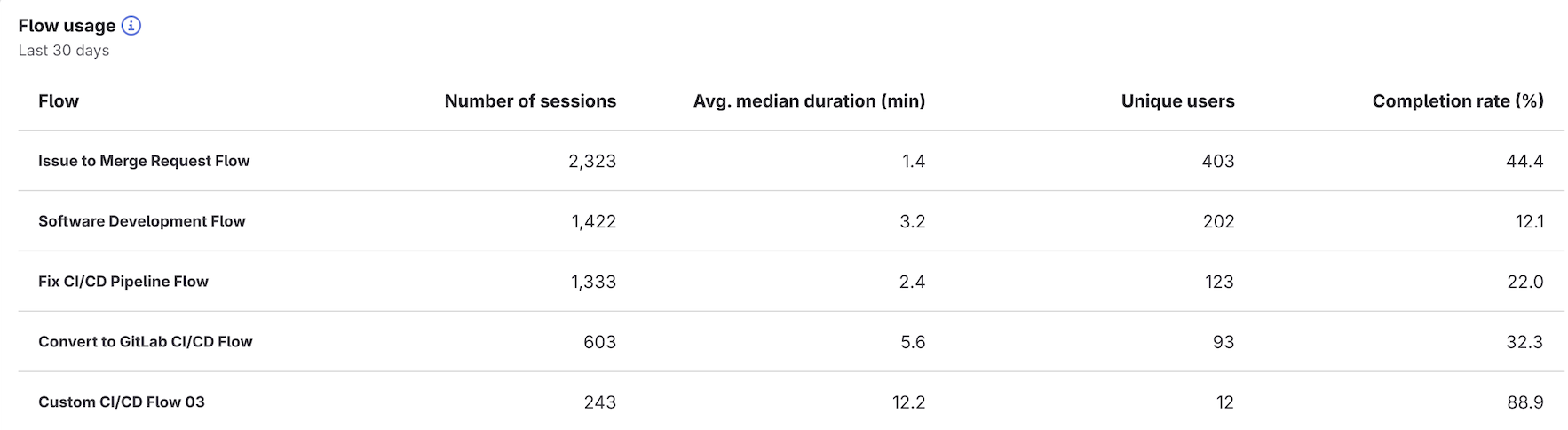
The Planner Agent now includes create and edit features in beta! The Planner Agent is a foundational agent built to support product managers directly in GitLab. Use the Planner Agent to create, edit, and analyze GitLab work items.
Instead of manually chasing updates, prioritizing work, or summarizing planning data, the Planner Agent helps you analyze backlogs, apply frameworks like RICE or MoSCoW, and surface what truly needs your attention. It’s like having a proactive teammate who understands your planning workflow and works with you to make better, more efficient decisions.
Please provide your feedback in issue 576622.
Dynamic input options in CI/CD pipelines
Dynamic input options in CI/CD pipelines
You can set up your CI/CD pipelines to make use of dynamic input selection when creating new pipelines through the intuitive web interface.
Now, with dynamic input options, you can configure your pipelines so that input selection options update dynamically based on previous selections. For example, when you select an input in one dropdown list, it automatically populates a list of related input options in a second dropdown list.
With CI/CD inputs, you can:
- Trigger pipelines with pre-configured inputs, reducing errors and streamlining deployments.
- Enable your users to select different inputs than the defaults from dropdown menus.
- Now have cascading dropdown lists where options dynamically update based on previous selections.
This dynamic capability enables you to create more intelligent, context-aware input configurations that guide you through the pipeline creation process, reducing errors and ensuring only valid combinations of inputs are selected.
SAST False Positive Detection with AI (Beta)
SAST False Positive Detection with AI (Beta)
Security teams often spend significant time investigating SAST findings that turn out to be false positives, diverting attention from genuine security risks.
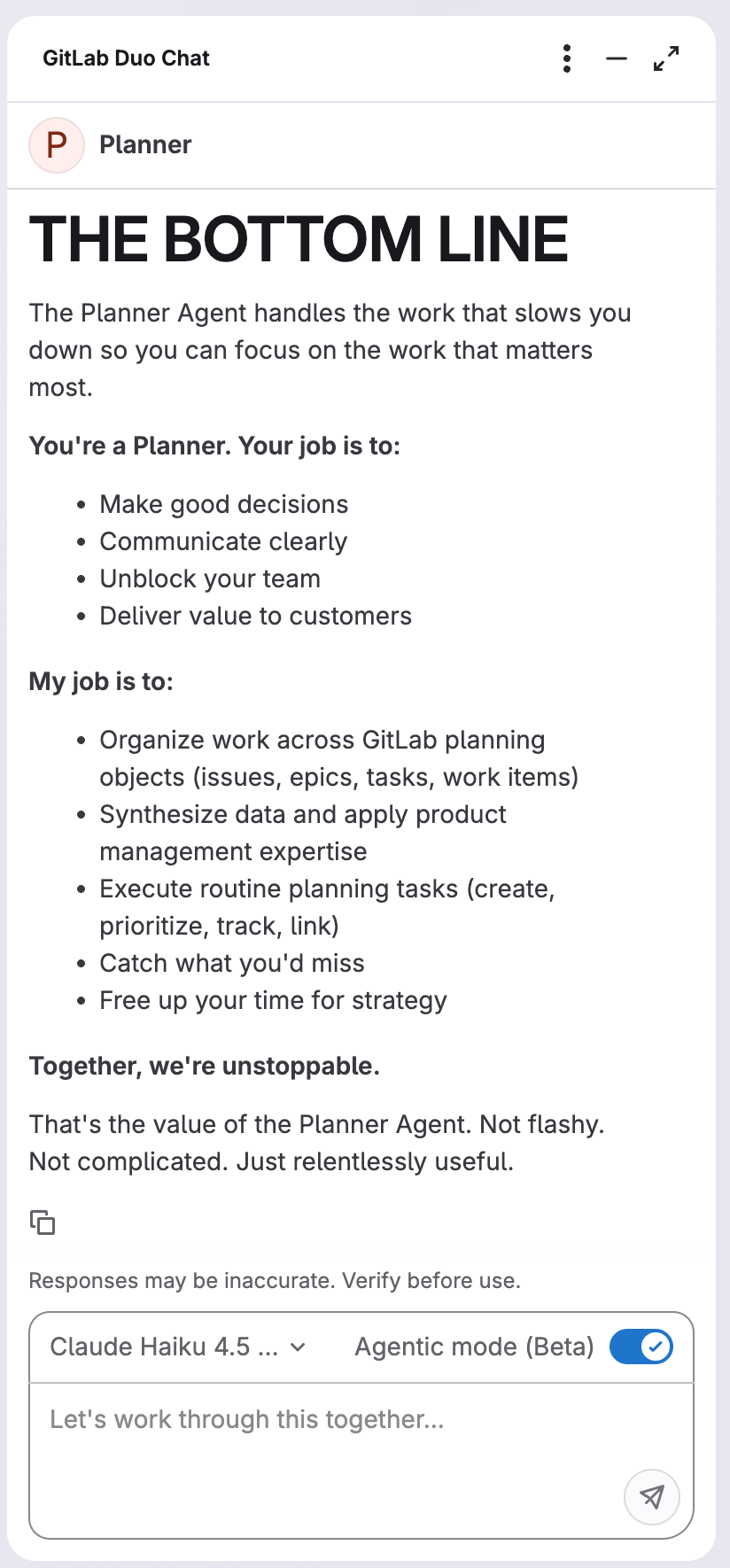
In GitLab 18.7, we’re introducing AI-powered SAST False Positive Detection to help teams focus on the vulnerabilities that matter. When a security scan runs, GitLab Duo automatically analyzes each Critical and High severity SAST vulnerability to determine the likelihood that it’s a false positive.
The AI assessment appears directly in the vulnerability report, giving security engineers immediate context to make faster, more confident triage decisions.
Key capabilities include:
- Automatic analysis: False positive detection runs automatically after each security scan with no manual triggering required.
- Manual trigger option: Users can manually trigger false positive detection for individual vulnerabilities on the vulnerability details page for on-demand analysis.
- Focused on high-impact findings: Scoped to Critical and High severity vulnerabilities to maximize signal-to-noise improvement.
- Contextual AI reasoning: Each assessment includes an explanation of why the finding may or may not be a true positive, based on code context and vulnerability characteristics.
- Seamless workflow integration: Results surface directly in the vulnerability report alongside existing severity, status, and remediation information.
This feature is available as a free beta for Ultimate customers and must be enabled in your group or project settings. We welcome your feedback in issue 583697.
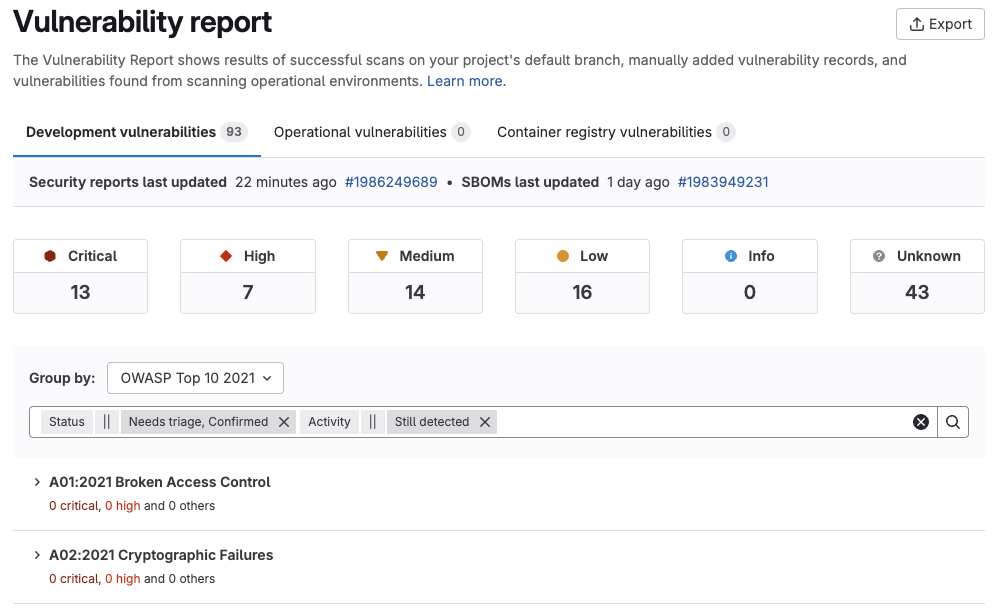
New security dashboards enabled by default
New security dashboards enabled by default
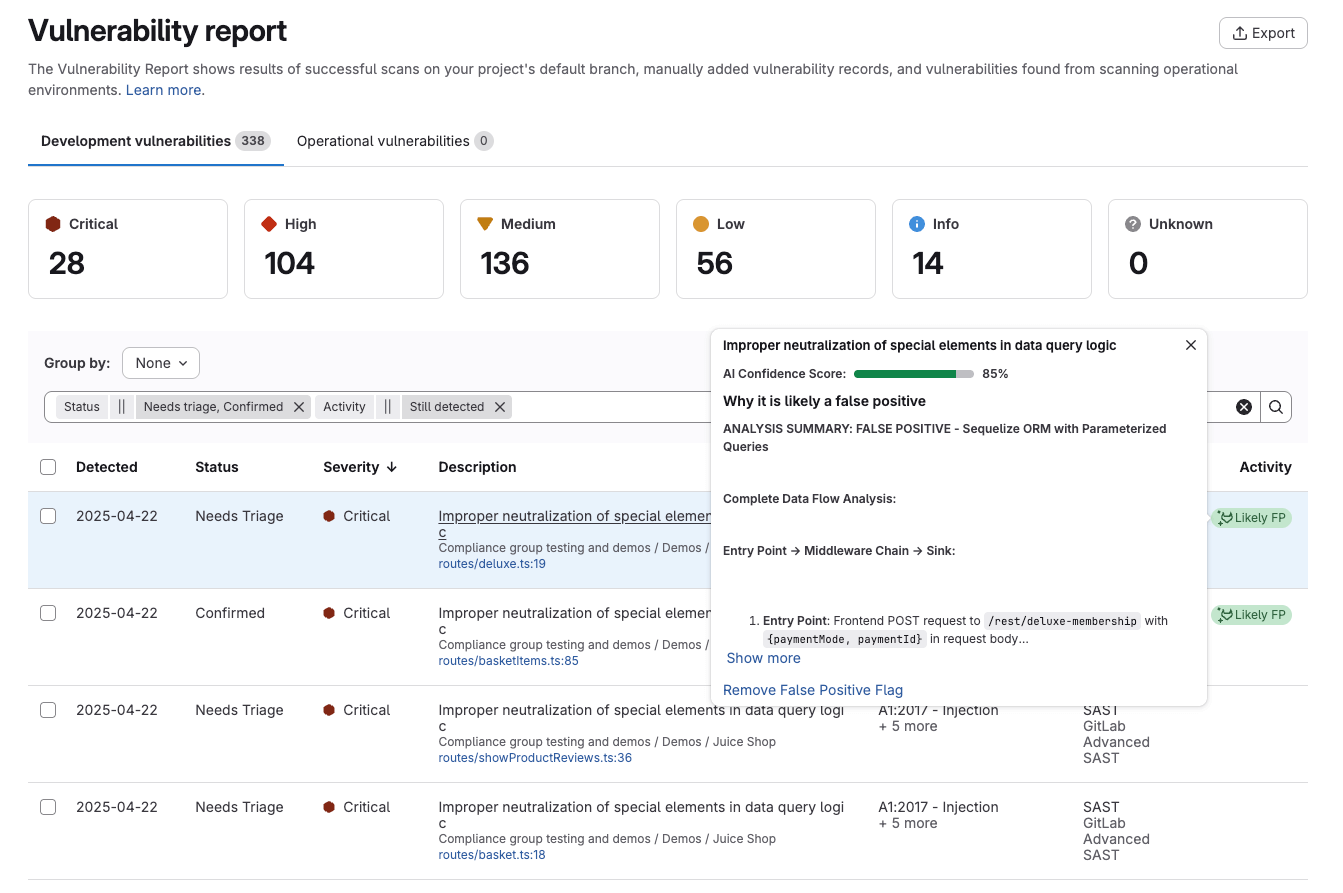
The new security dashboards have been updated and modernized. The dashboards were previously available on GitLab.com, and are now enabled by default on GitLab Dedicated and GitLab Self-Managed.
The new features include:
- A vulnerabilities over time chart that supports:
- Filtering based on project or report type.
- Grouping by report type and severity.
- Direct links to vulnerabilities in the vulnerability report.
- A risk score module that calculates the estimated risk for a group or project based on a GitLab algorithm.
Please note that using the new dashboard requires ElasticSearch.
Instance setting to control publishing of components to the CI/CD Catalog
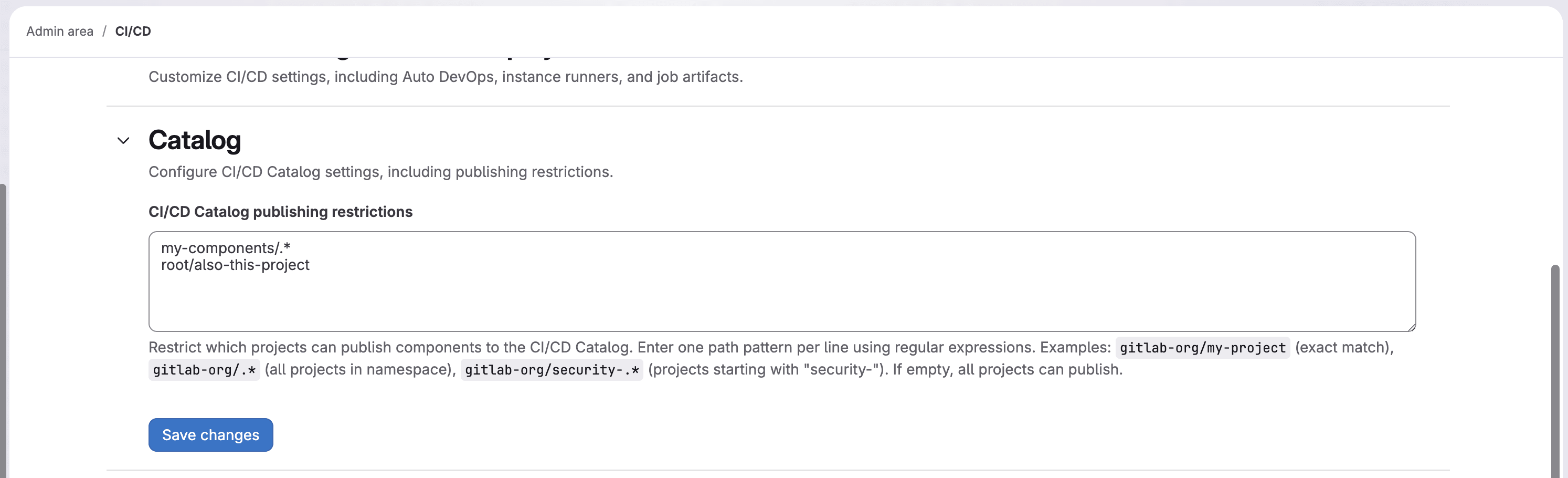
Instance setting to control publishing of components to the CI/CD Catalog
Administrators of GitLab Self-Managed and GitLab Dedicated can now restrict which projects are allowed to publish components to the CI/CD Catalog. This new setting enables organizations to maintain a curated, trusted CI/CD Catalog by controlling what components can be published.
Administrators can now specify an allowlist of projects authorized to publish components. When the allowlist is populated with projects, only those projects can publish components. This prevents unauthorized or unapproved components from cluttering the list of published components and ensures all components meet organizational standards and security requirements.
This addresses a key governance challenge for enterprise customers who want to maintain control over their CI/CD component ecosystem while enabling their teams to discover and reuse approved components.


We want to hear from you
Enjoyed reading this blog post or have questions or feedback? Share your thoughts by creating a new topic in the GitLab community forum.
Share your feedback